New Features in Splunk SOAR 6.3
Wayfinder
Wayfinder is a dynamic navigation tool within Splunk SOAR designed to help you move around the Splunk SOAR user interface quickly and easily. By using straightforward keyboard shortcuts, you can jump directly to key incidents, automation playbooks, and other critical information without wading through multiple menus. Wayfinder enhances your experience by making navigation intuitive and efficient.
Playbook Building with Natively Integrated SIEM and SOAR
In Splunk SOAR 6.3, SOAR features now come fully integrated with Splunk Enterprise Security 8.0. In this demo, see how to easily create a Splunk SOAR playbook in the context of your SIEM workflows. Playbooks and actions are now directly integrated within the Splunk Enterprise Security analyst queue. You can run playbooks and see the results without leaving the Splunk Enterprise Security interface. A Splunk SOAR and Splunk Enterprise Security license is required.
Features
Main Dashboard
Splunk SOAR’s customizable main dashboard allows users to track key metrics such as mean time to detect and respond, time and dollars saved, and much more. You can adjust the location of dashboard panels to ensure you have the information that matters most to you right at your fingertips.
Apps
Splunk SOAR integrates across 300+ third-party tools and supports 2,800+ automated actions via our catalog of connectors on Splunkbase. This allows you to connect and coordinate complex workflows across your teams and tools, so you don’t need to rip and replace your existing stack. All Splunk SOAR apps are available on Splunkbase.
App Editor
In addition to our out-of-the-box apps, Splunk SOAR also allows you to create custom apps to best fit the use cases that matter most to you. With Splunk SOAR's App Editor, you can easily view and add code, test actions, see log results and troubleshoot. This additional visibility into how well your app works enables you to iterate it to suit your needs and evolve as your SOC evolves.
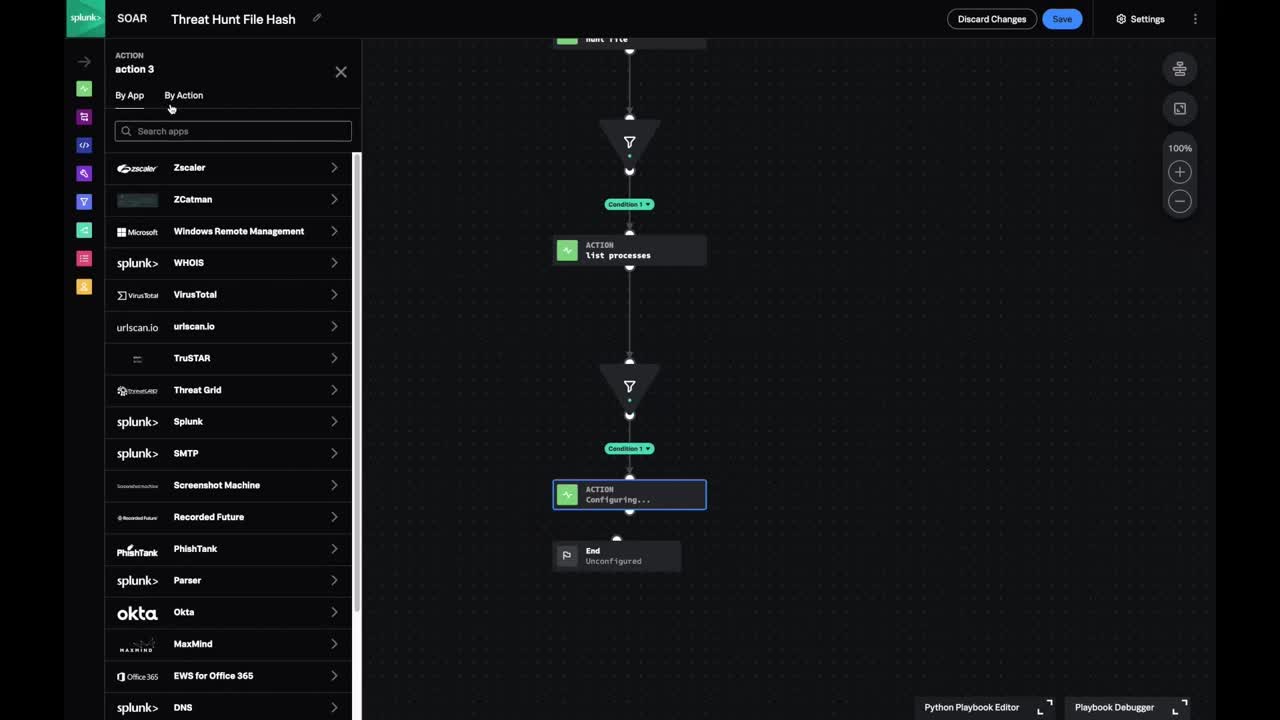
Visual Playbook Editor + Input Playbooks
Whether you’re new to coding or a Python expert, Splunk SOAR provides you with the means to create and customize playbooks. The Visual Playbook Editor simplifies the playbook creation process by allowing you to assemble custom workflows with prebuilt code blocks and action strings. Splunk SOAR also features input playbooks for basic IT tasks, which can be integrated into larger playbooks and security workflows. With a variety of prebuilt playbooks, you can immediately start automating.
Case Management
Splunk SOAR orchestrates workflows and responses across your security and IT stack so that each tool is active in your defense strategy. Case management functionality uses workbooks to codify your processes into reusable templates. Whether you're using custom templates or industry standards for incident response, Splunk SOAR facilitates task segmentation, assignment, and documentation, ensuring a cohesive and collaborative investigative process.
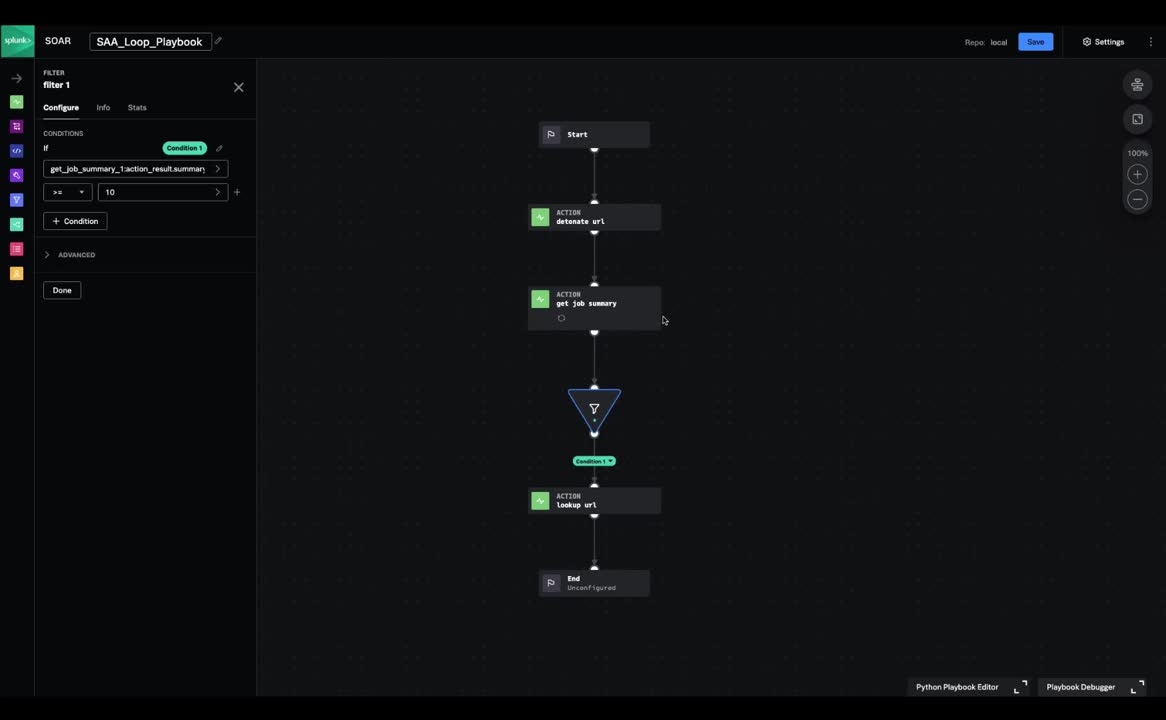
Logic Loops
Logic Loops are a feature in Splunk SOAR that allow users to reduce the operational complexity of building and maintaining playbooks that require repeatable looping functionalities without having to write their own custom code. This iterative function allows users to automatically retry playbook actions if they fail, or continue with the rest of the playbook when the action succeeds. This function can be applied to use cases like sandbox engines for malicious URL quarantine and remediation as well as forensic investigation workflows.
Custom Functions
Splunk SOAR’s custom functions allow you to share custom code across playbooks while introducing complex data objects into the execution path. These aren’t just out-of-the-box playbooks, but out-of-the-box custom blocks that save you time and effort. These capabilities provide the building blocks for scaling your automation, even to those without coding capabilities.
Contextual Action Launch
Splunk SOAR apps have a parameter for action inputs and outputs called "contains". These are used to enable contextual actions in the Splunk SOAR user interface. A common example is the contains type "ip". This is a powerful feature that the platform provides, as it allows the user to chain the output of one action as input to another.
Investigation Command Line
When you're on the Splunk SOAR investigation page, there are several ways to run actions. One of the easiest ones is to use the command line, down where you would write comments in the event. If you start off with a slash (/) you get prompting for the action you would like to choose.
Configure Third Party Tools
To get started in Splunk SOAR, you will need to configure an asset. Assets are the security and infrastructure assets that you integrate with the Splunk SOAR platform, like firewalls and endpoint products. Splunk SOAR connects to these assets through apps. Apps extend the platform by integrating third-party security products and tools.
Splunk SOAR Playbooks
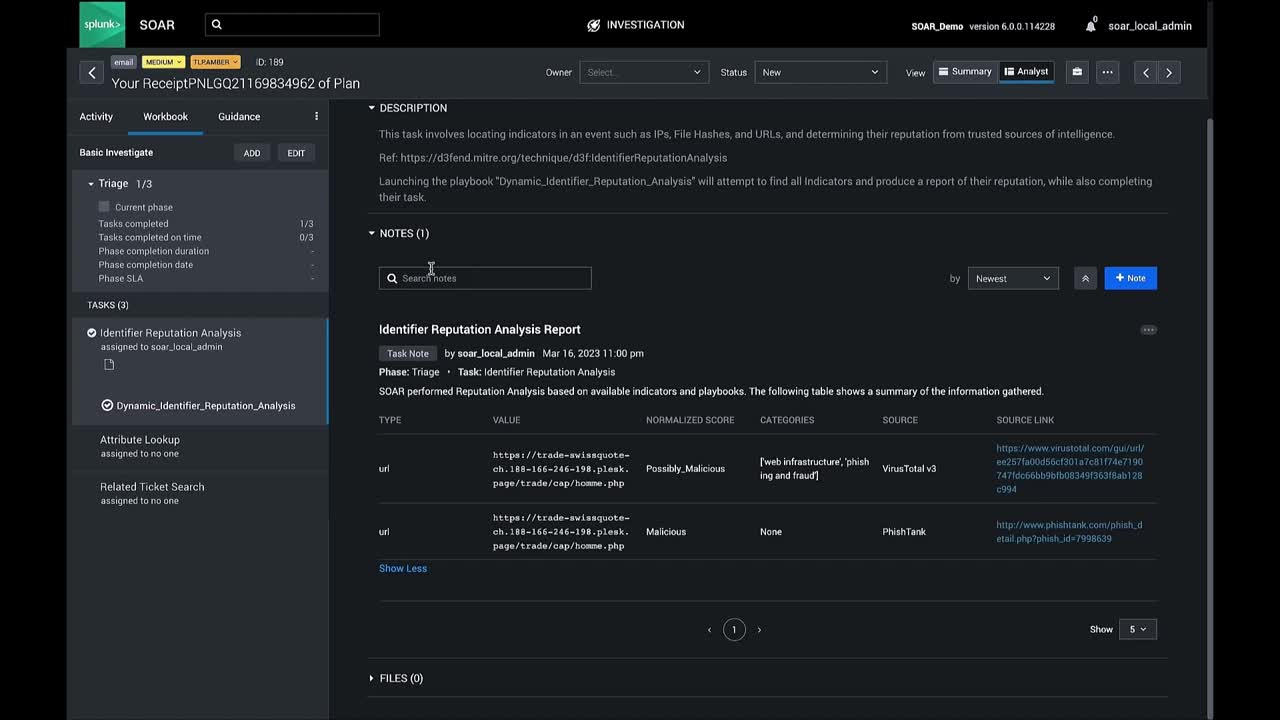
Dynamic Identifier Reputation Analysis
The Dynamic Identifier Reputation Analysis playbook is an essential tool for any security operations center (SOC) team looking for a comprehensive view of their environment’s threat landscape. By leveraging MITRE DEFEND's approach for dynamic identifier reputation analysis, SOC teams can quickly identify potential threats and vulnerabilities and take proactive steps towards mitigating risk before it causes damage.
Splunk Intelligence Management for Splunk SOAR
While Splunk SOAR playbooks automate security actions, they become even more powerful and easy to use with the addition of Splunk ES’s Intelligence Management. This allows users to intake prepared and normalized intelligence from internal and external sources for faster triage and more streamlined playbooks.