Splunk SOAR Playbook of the Month: Tackling Phishing Attempts with Identifier Reputation Analysis

Security professionals have become all too familiar with the threat posed by phishing. Whether it’s a convincing looking email asking an employee to click a link to update their login credentials or a surprise text from the CEO asking them to send over gift card codes for a customer, phishing attacks have only continued to grow over the years.
For 2023 alone, 33 million data records are expected to be compromised due to phishing attacks. With so many potential threats poised to end up in employees' inboxes, how can security teams prevent these potential threats before they turn into security incidents?
Fortunately, Splunk SOAR offers a powerful set of enrichment response playbooks that can help identify malicious threats like these based on digital identifiers. For this month’s edition of Playbook of the Month, we’ll look at one set of playbooks from Splunk SOAR’s enrichment response pack, that focuses on Identifier Reputation Analysis.
What Is Identifier Reputation Analysis?
Identifier Reputation Analysis (IRA) is a method used in cybersecurity and digital forensics to evaluate the trustworthiness or risk associated with a digital identifier, such as IP addresses, email addresses, domain names, or usernames. The goal of IRA is to detect and mitigate potential threats by analyzing the historical behavior and reputation of these identifiers.
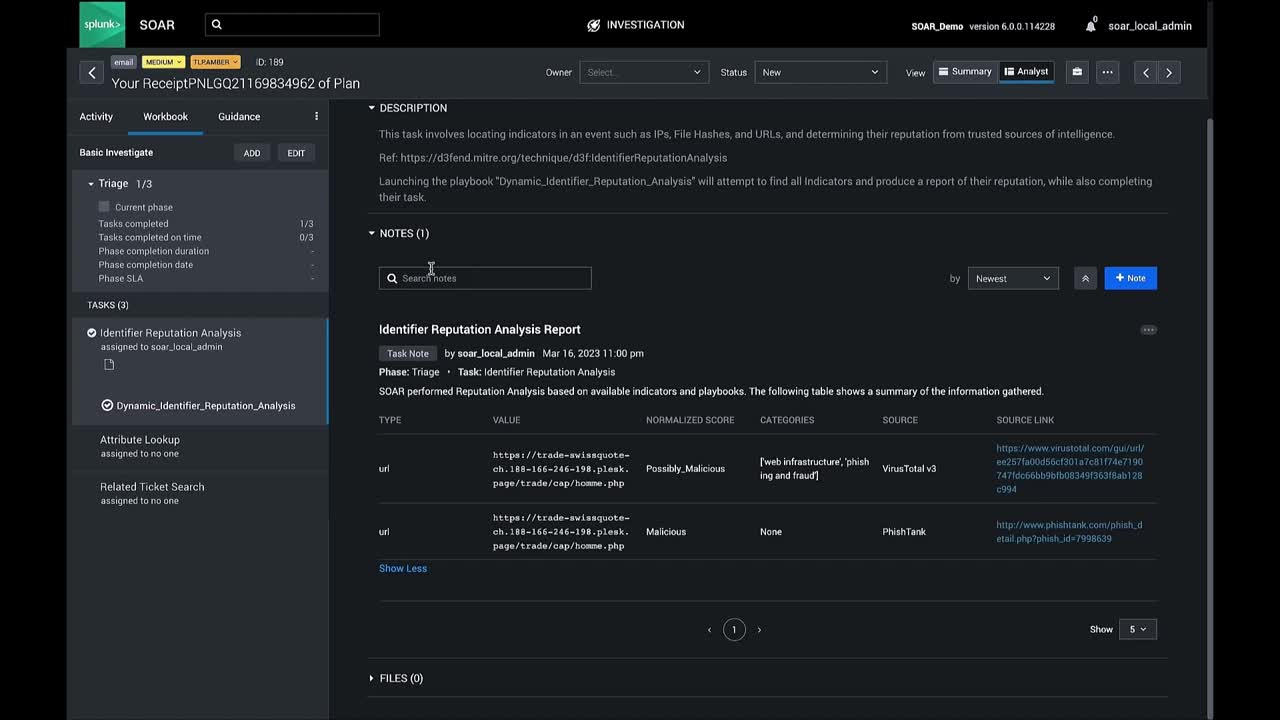
The Dispatch Identifier Reputation Analysis playbook is an essential tool for any security operations center (SOC) team looking for a comprehensive view of their environment’s threat landscape. By leveraging MITRE D3FEND’s approach for identifier reputation analysis, SOC teams can quickly identify potential threats and vulnerabilities and take proactive steps towards mitigating risk before it causes damage.
The Playbook
The Dispatch Identifier Reputation Analysis playbook automatically enriches an incident with reputation details using pre-built community playbooks from VirusTotal and PhishTank. Here’s how to use it:
- Set up the VirusTotal connector by entering your API key (obtainable for free from VirusTotal) and testing connectivity.
- Set up the PhishTank connector (pre-configured).
- Locally save the associated playbooks for MITRE DEFENSE mapping and VirusTotal v3.
- Add these playbooks to the response task.
- Save the parent playbook that calls both playbooks, then add it to the response task.
And with that, the Identifier Reputation Analysis Playbook is ready to use.
Watch the video to see how the pre-built workflow for Identifier Reputation Analysis can be used in action and how it improves your organization’s threat landscape.
Taking It a Step Further
Suppose a SOC team wants to incorporate helper playbooks into their custom workflow. Let’s take an example where a SOC needs to receive alerts via email for specific malware indicators with reputation scores tagged on them. We will use Splunk SOAR to accomplish this task in just a few simple steps:
- Pull in a pre-built playbook: We will start by searching for pre-built playbooks associated with our VirusTotal v3 connector. We will select the VirusTotal_v3_Identifier_Reputation_Analysis playbook.
- Analyze the playbook: By clicking on the START and END blocks of the playbook, we can get an idea of its inputs and outputs. We can customize the normalization process by adjusting the logic.
- Create a new playbook: In the playbook editor, we will create a new Automation playbook and call our VirusTotal playbook.
- Test the playbook: After saving the playbook with a commit message, we can test it against an event to ensure that it produces the desired output.
- Filter and block URLs: We can use a filter block to block URLs with a reputation score greater than or equal to 8. We can then use the “Action” block to select ZScaler and pick “Block URL.”
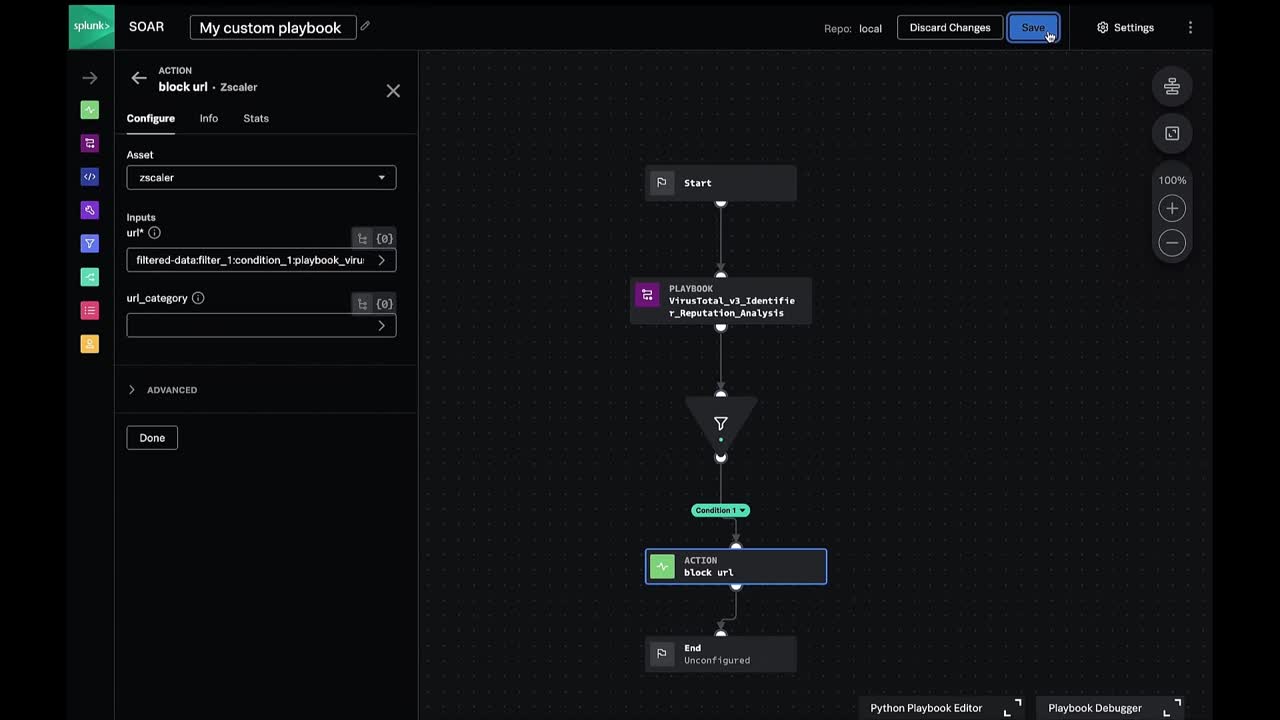
With the steps above, we have customized our workflow on top of a pre-built helper playbook that normalized reputation scores from VirusTotal.
This example shows how easy it is to build a custom workflow using Splunk SOAR. With its powerful tools and capabilities, Splunk SOAR enables SOC teams to automate workflows and streamline their security operations. Be sure to check out research.splunk.com/playbooks to explore even more useful playbooks. We look forward to hearing about your experience with this month’s featured playbooks as well as any other playbooks you’ve recently implemented. We’ll be back next month with more playbooks and demos, but until then, get out there and get automating!
Related Articles
About Splunk
The world’s leading organizations rely on Splunk, a Cisco company, to continuously strengthen digital resilience with our unified security and observability platform, powered by industry-leading AI.
Our customers trust Splunk’s award-winning security and observability solutions to secure and improve the reliability of their complex digital environments, at any scale.


