Automate repetitive tasks, take care of security incidents in seconds and increase analyst productivity.
Solution
Respond to threats and incidents faster with security automation.
Work smarter, not harder
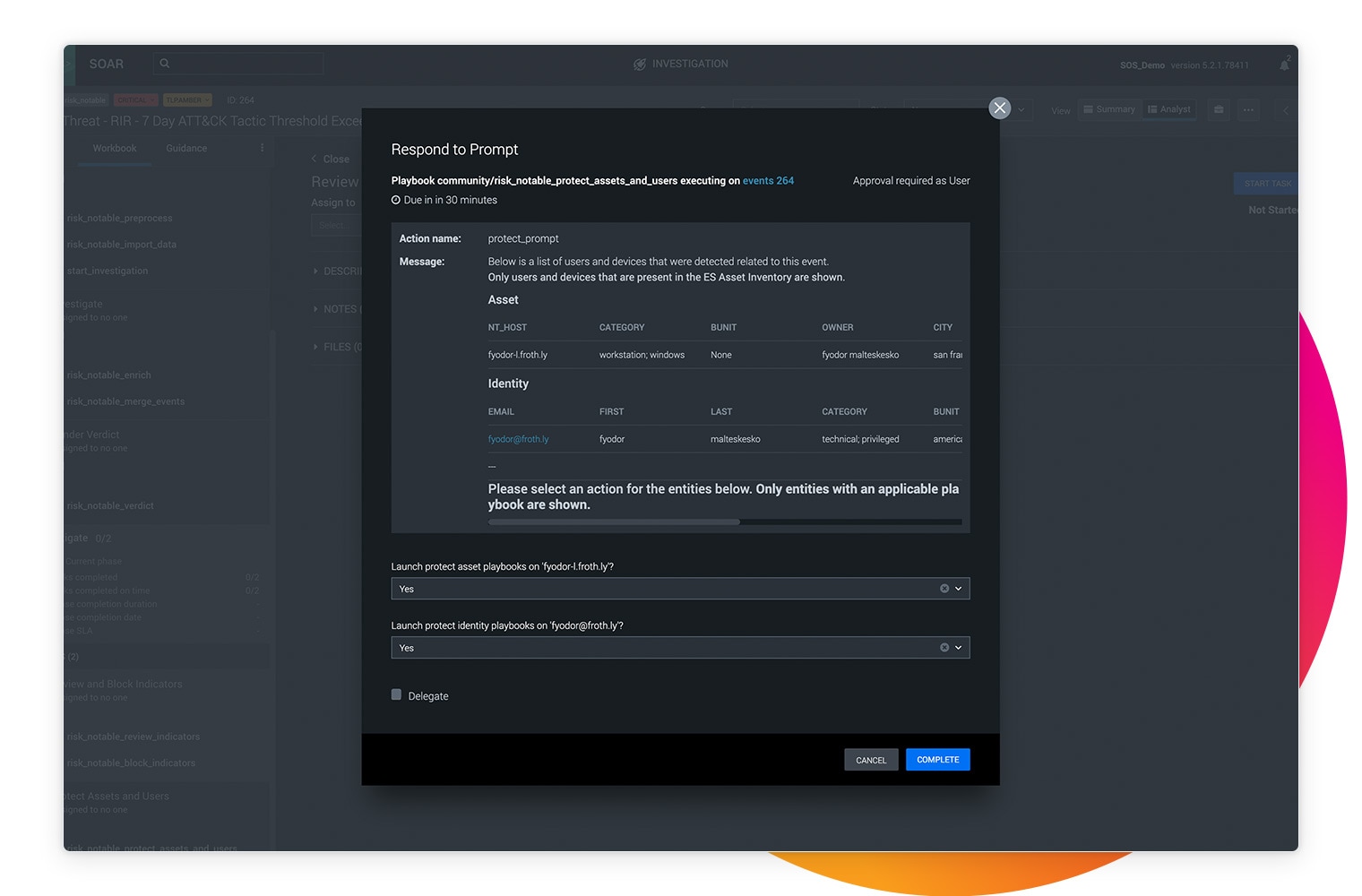
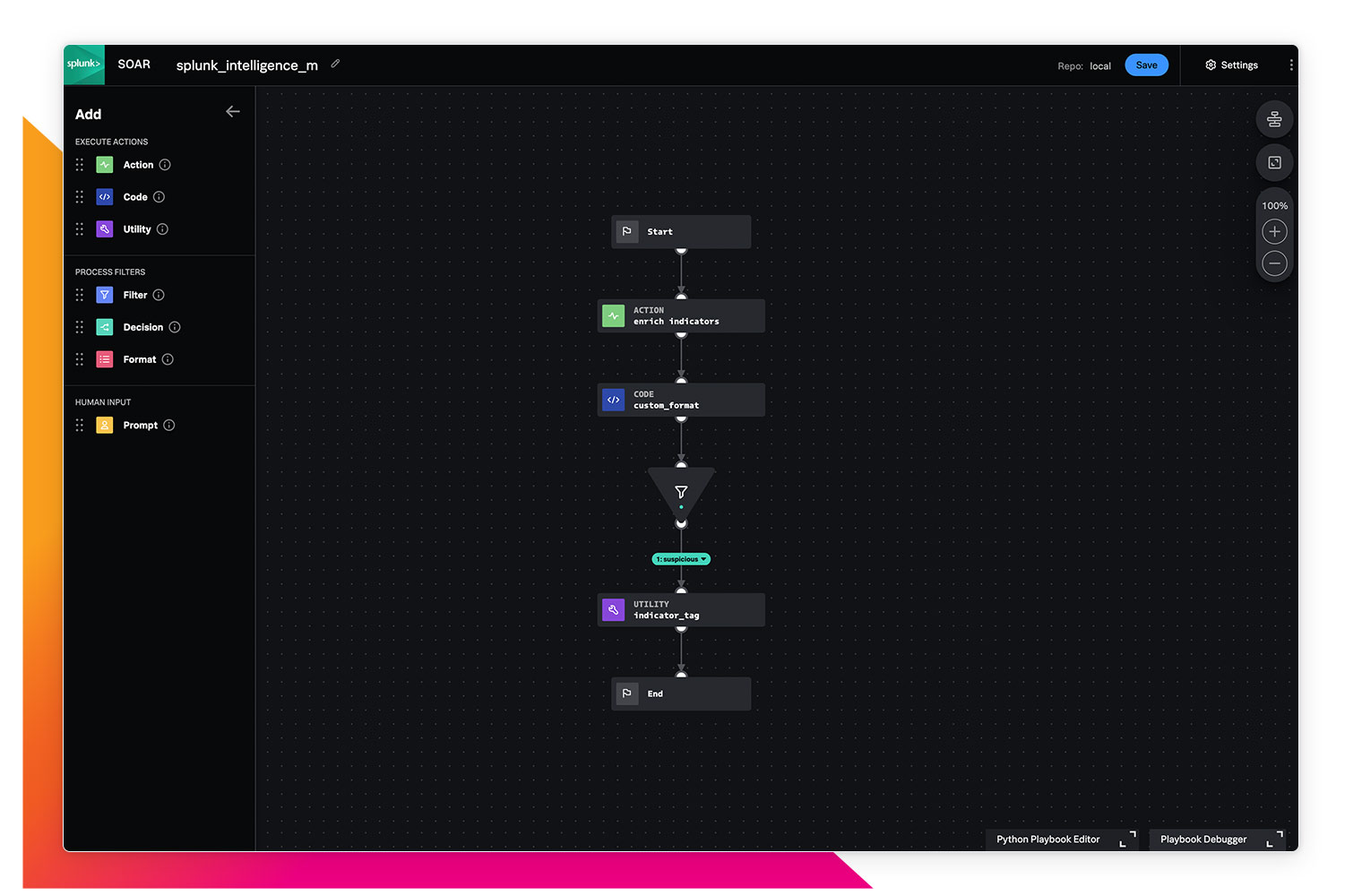
Automate your manual security tasks to streamline your team and processes.
From overwhelmed to in control
Stop being reactive, and use automation to create a proactive security practice.
Security at machine speed
Threats move fast. Move faster with automated investigation and response.
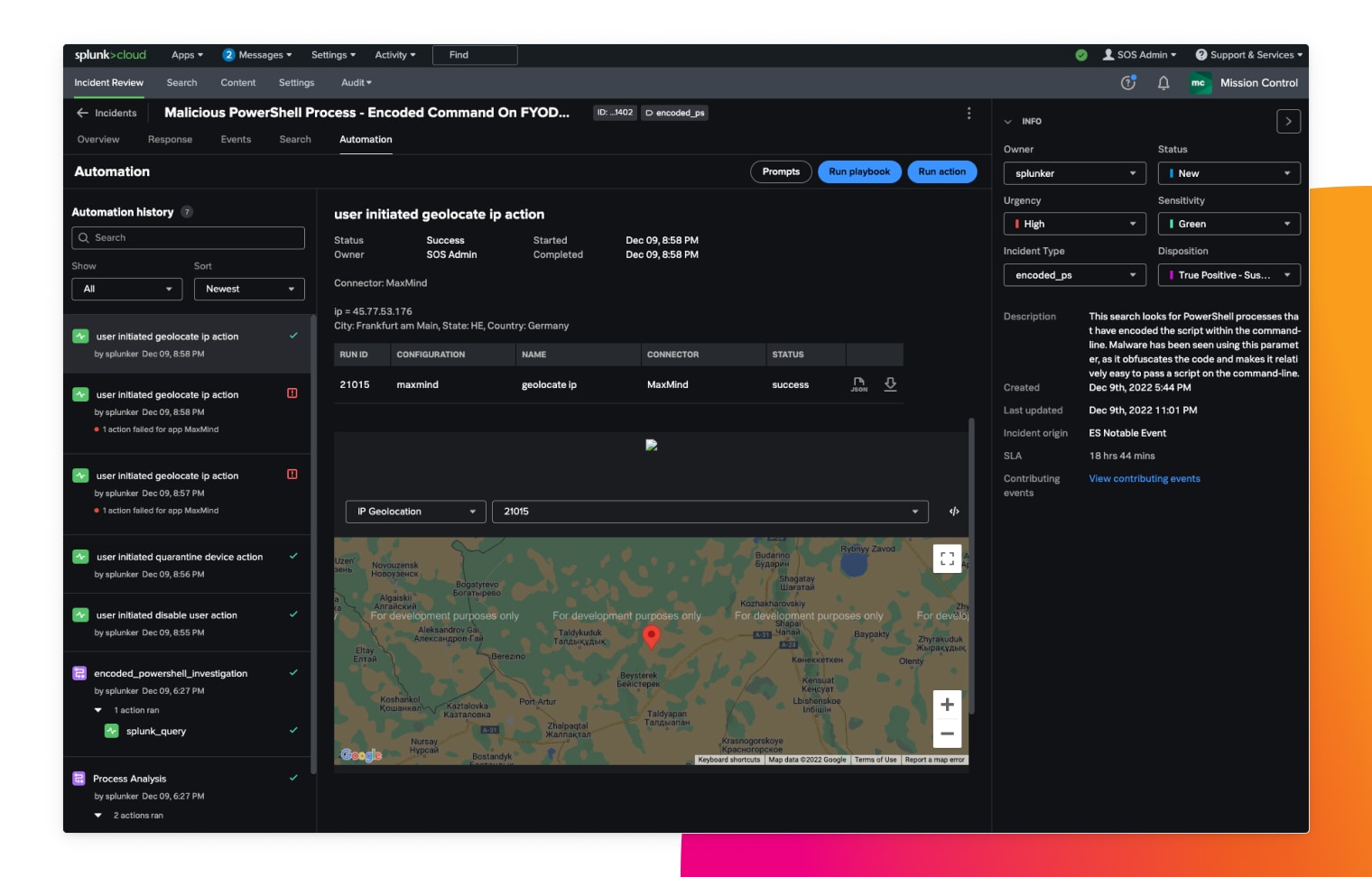
From 30 minutes to 30 seconds
Address threats in seconds — not minutes or hours. Lower your mean time to respond (MTTR) to threats using playbooks that automate security tasks across a multitude of tools at machine speed.
Splunk SOAR makes it easy to educate our engineers and enlist them as allies to the TDR team. That means we’re effectively expanding the number of people safeguarding our infrastructure and providing higher levels of assurance that our data is safe.
Eliminate grunt work
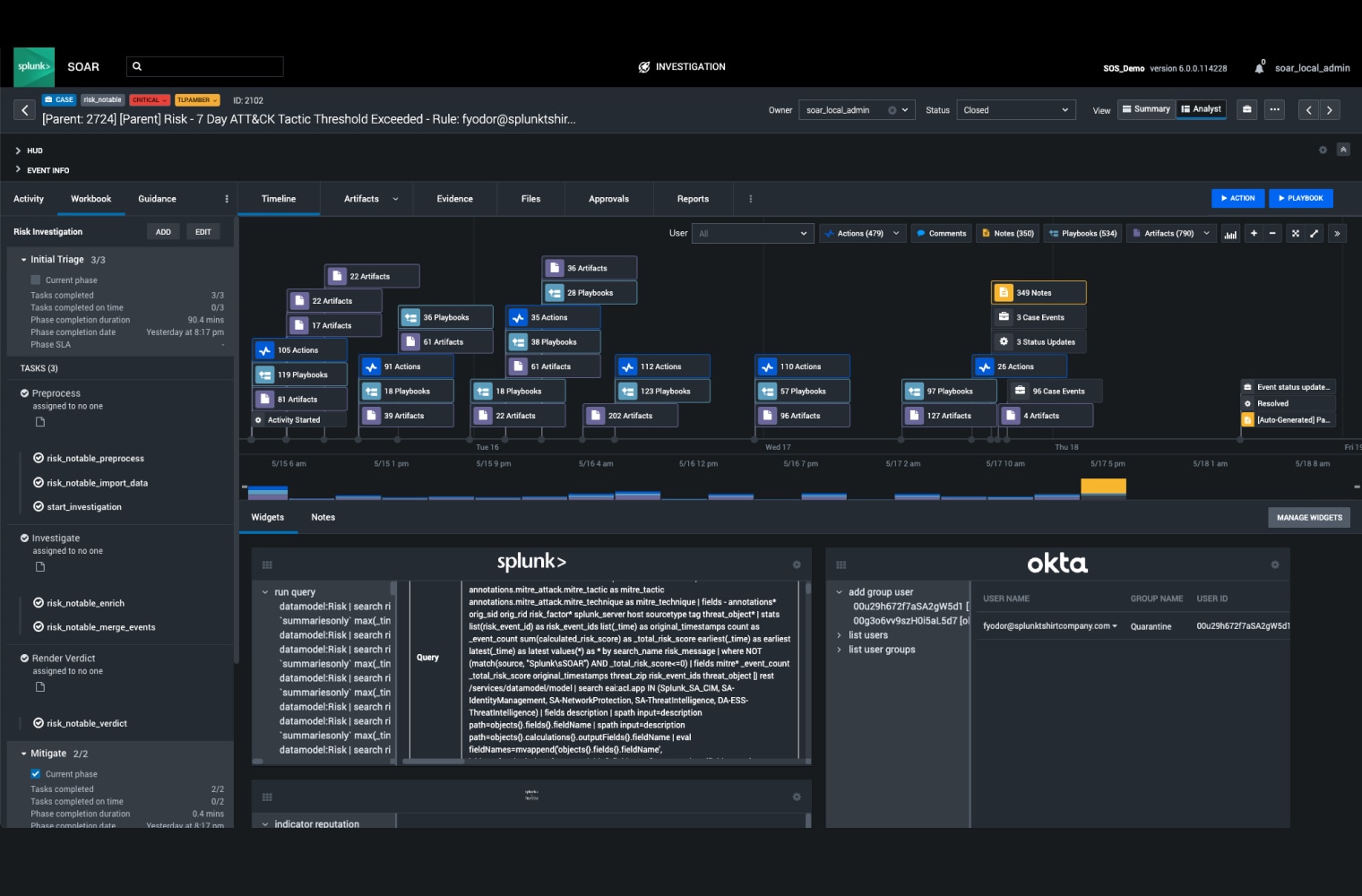
Maximize your security team's efficiency, productivity, and autonomy using Splunk SOAR. By automating repetitive tasks and investigations, you can reclaim precious time and resources to focus on the tasks that matter most to your organization.
With Splunk SOAR, we achieved the equivalent workload of 10 full-time employees, completed by just a small team of analysts, within the first 6 months of the year.
Streamline workflows with pre-defined templates
Splunk Mission Control helps security teams streamline their workflows with predefined templates, build repeatable processes, measure and audit response times, and embed searches to speed up investigations. Collected data can be used to track task duration, identify bottlenecks and improve operations with automation.
GoTo sees Splunk Mission Control as a solution that can take its security operations to the next level. The more we can centralize our SOAR, threat intelligence and ticketing system data in Mission Control, the more time we can save.