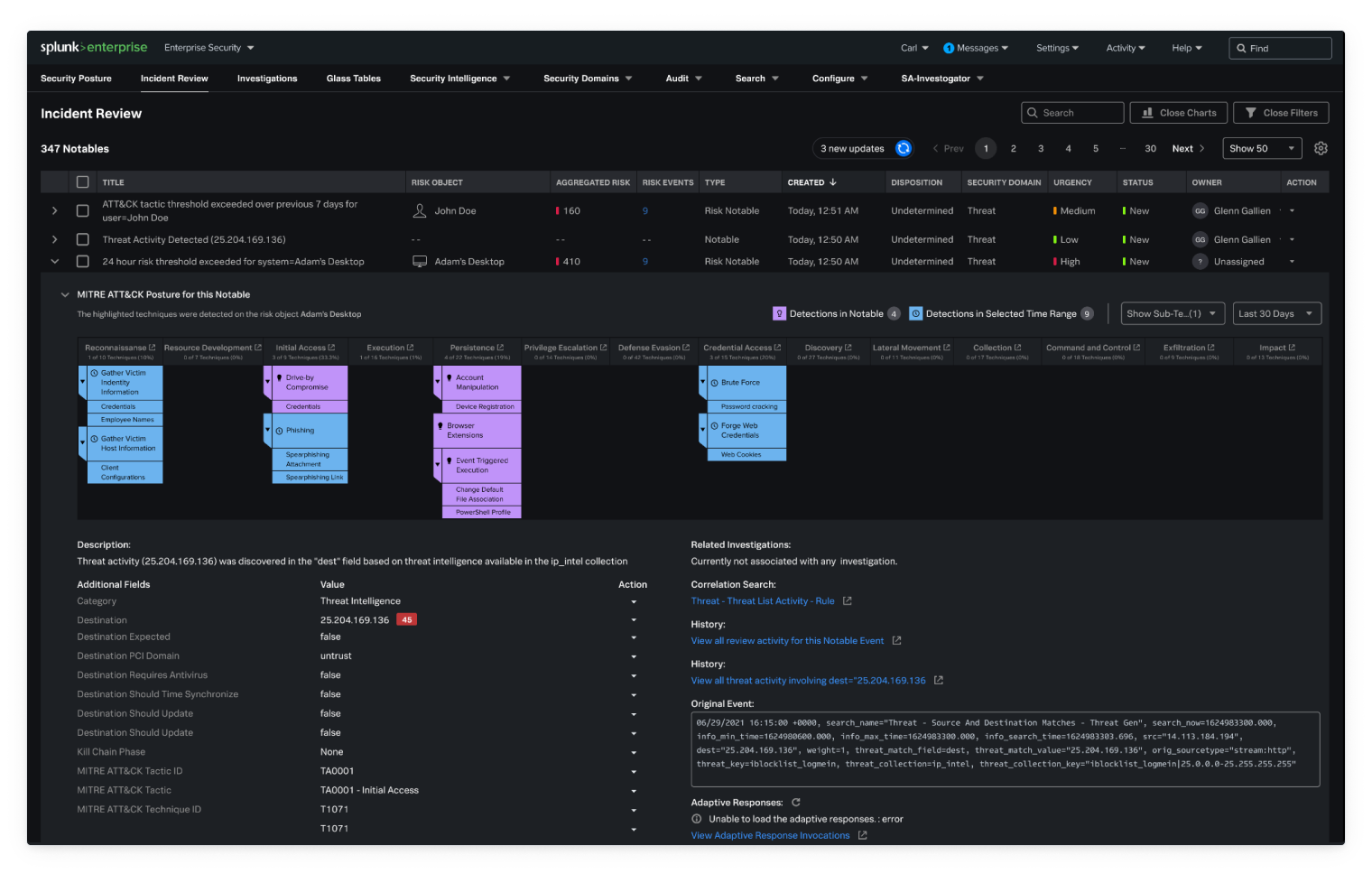
Market-leading SIEM to quickly detect, investigate, and respond to threats.
solution
Rapidly detect Advanced Persistent Threats (APT)
Spot anomalies
Monitor for malicious behavior and stop it fast.
Enrich with threat intelligence
Combine internal and external intelligence data to get a holistic view of security threats.
Detect in seconds
Use real-time streaming analytics to quickly detect suspicious and malicious behaviors.
Combat threats with actionable analytics
Protect your business and mitigate risk at scale with data-driven insights from Splunk Enterprise Security.
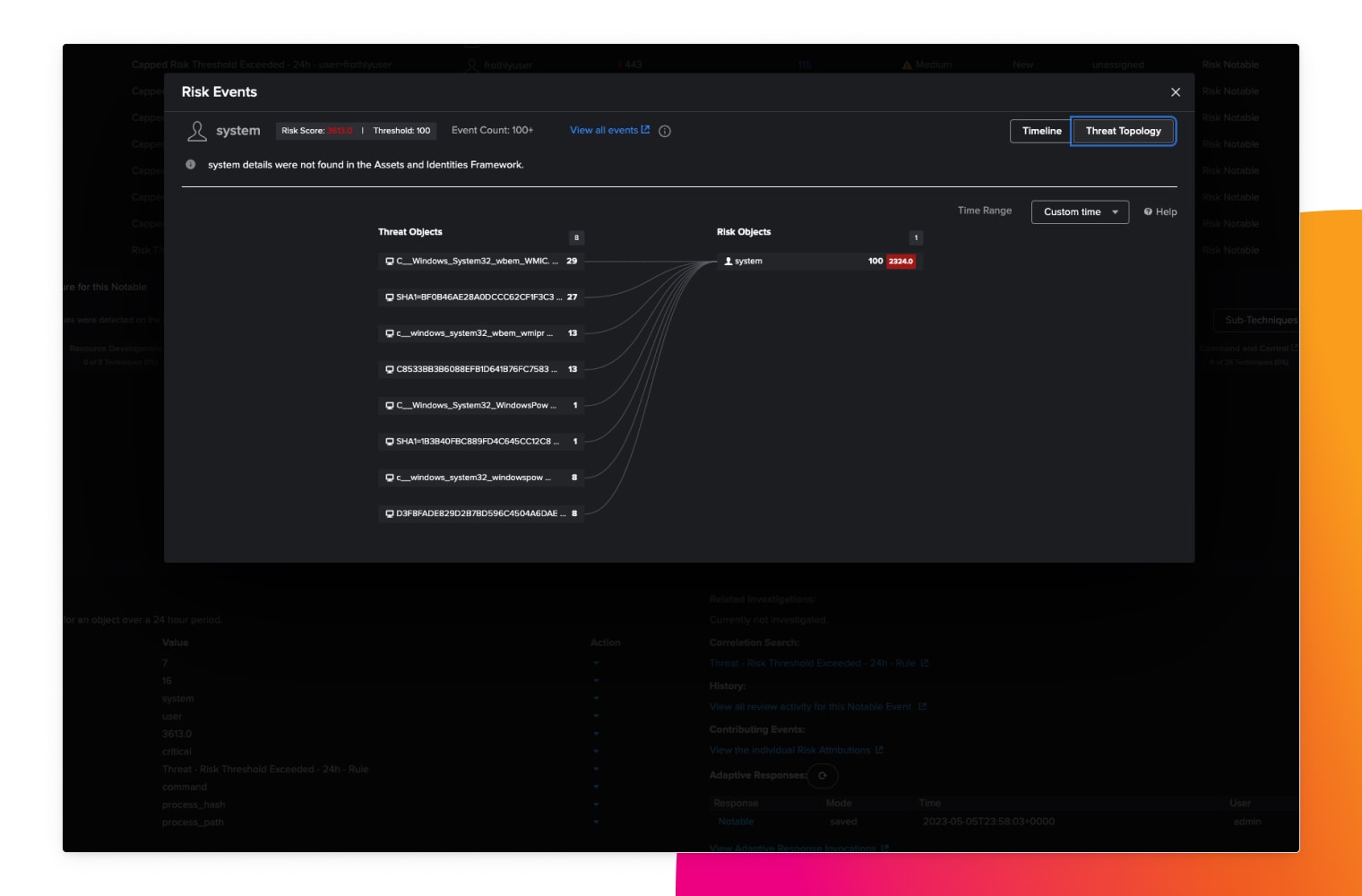
Risk-based alerting
Conquer alert fatigue, attribute risk to users and systems, map alerts to cybersecurity frameworks and trigger alerts when risk exceeds thresholds.
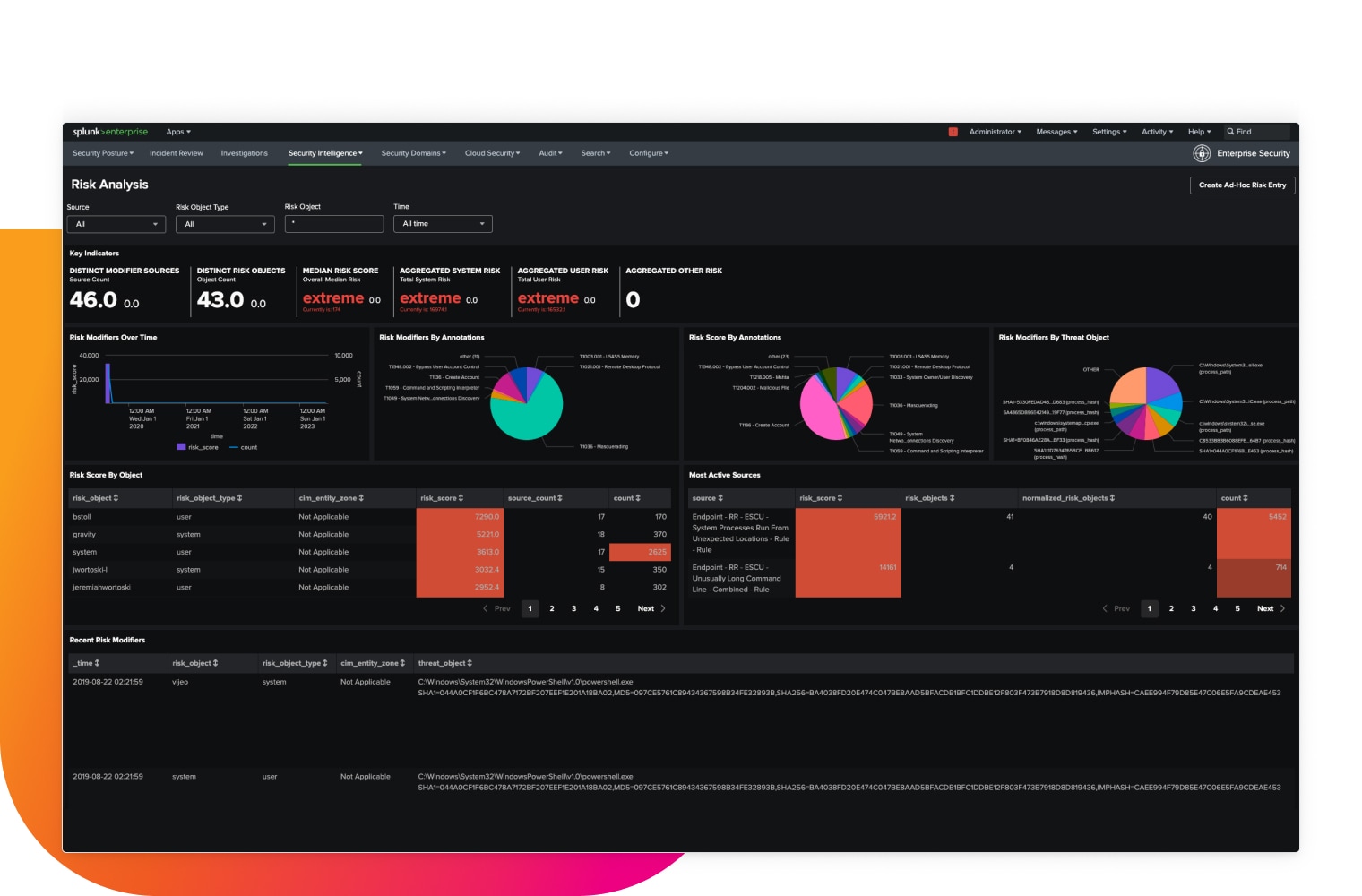
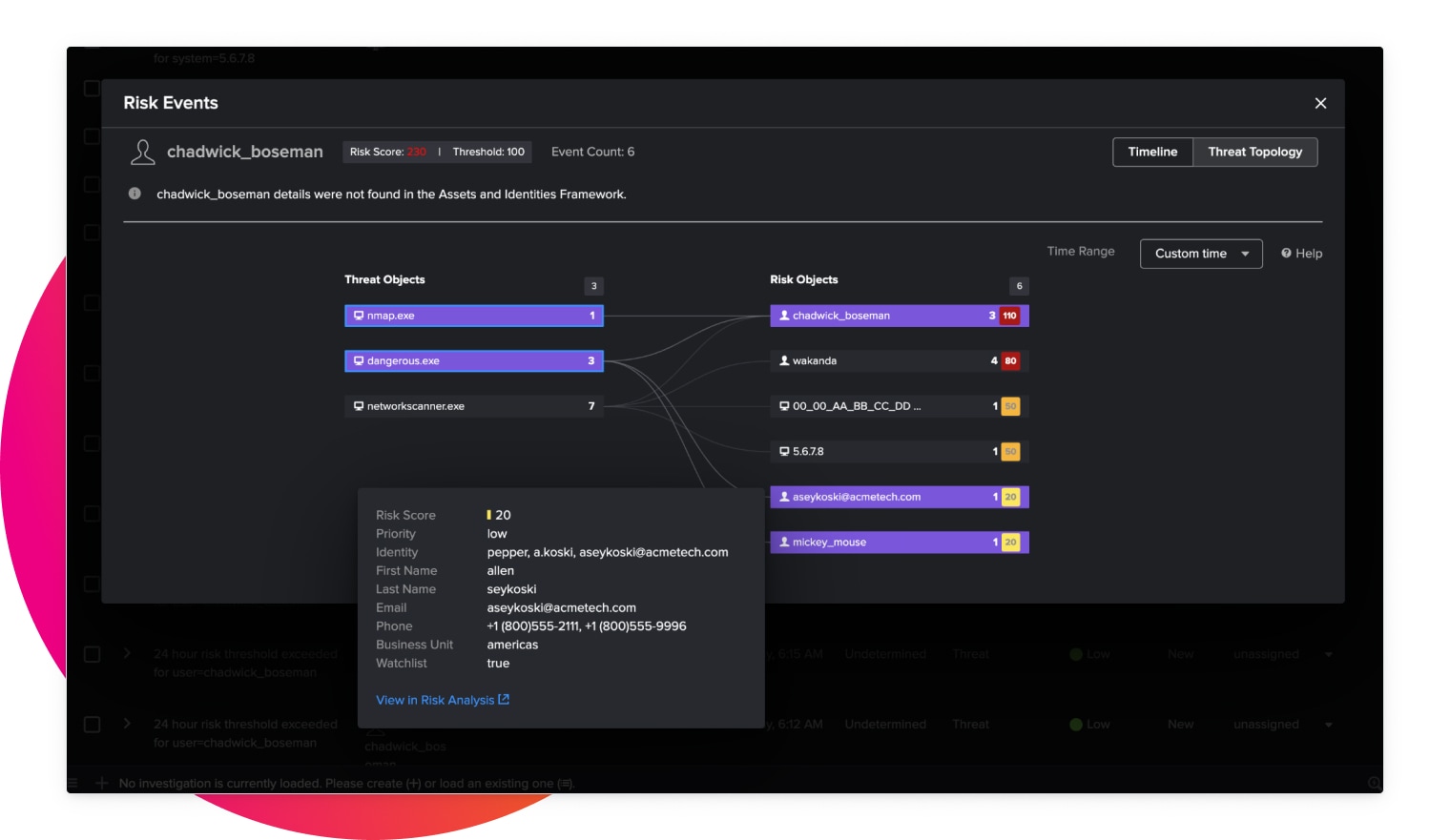
Scalable real-time streaming analytics
Our advanced security detections enable better situational awareness and rapid response times to suspicious behavior. They effectively combat insider threats, credential access and compromise, lateral movement and living off the land.
Replacing our previous SIEM with Splunk Enterprise Security has dramatically improved our ability to effectively monitor and secure our complex hybrid environment. At the same time, using Splunk Cloud has helped ensure we have the flexibility we need to respond to the evolving threat landscape.